iClear Summary
The “iClear Summary” section allows you to view detailed information and statistical data about the third-party services summary workflow.
To view the summary data, go to the Fraud and Anomaly > iClear > iClear Summary section.
Note that the corresponding third-party service should be set and configured to collect and display the statistical information.
The section contains four tabs:
- The “Email Hygiene” tab
- The “IP Analysis” tab
- The “Phone Number Analysis” tab
- The "Companies House" tab
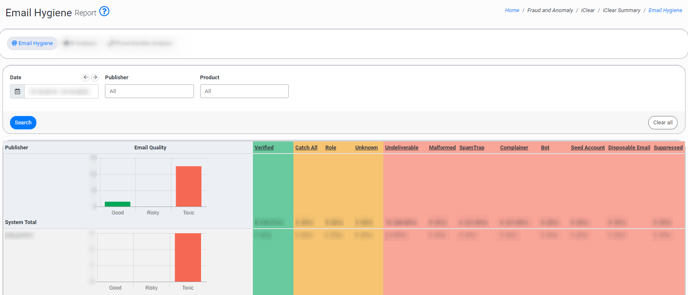
The “Email Hygiene” tab
The “Email Hygiene” tab allows you to view summary details about the “Email Hygiene” third-party service results. The third-party service gives a corresponding status to each email that is processed.
Read more about the “Email Hygiene” service in this Knowledge Base article.
You can narrow down the search results by using the following filters:
- Date: Select the date range of the report.
- Publisher: Select the Publisher.
- Product: Select the Product.
The report contains the following information. Please note that the first row of the report contains summary details across the system.
- Publisher: The name of the Publisher.
- Email Quality: The field contains the graph summarizing the results of service processing. The numbers are split by the general categories (Good, Risky, Toxic), and the total number of emails processed through the system is a sum of the values in the Good, Risky, and Toxic columns. The detailed summary by metrics is displayed in the columns of the report.
- Verified: The number of emails in the “Verified” category along with the percentage ratio of the total number of emails processed through the service to the number of emails in the particular category. The “Verified” status means that the email address is deliverable.
- Catch All: The number of emails in the “Catch All” category along with the percentage ratio of the total number of emails processed through the service to the number of emails in the particular category. The “Catch All” status means that the domain of the email address accepts all mail, and it is impossible to determine validity. If the email address was acquired organically or you have confidence in the validity of the email address, then send it at your discretion.
- Role: The number of emails in the “Role” category along with the percentage ratio of the total number of emails processed through the service to the number of emails in the particular category. The “Role” status means that the email is associated with common distribution groups such as abuse@, sales@, no-reply@, test@, etc.
- Unknown: The number of emails in the “Unknown” category along with the percentage ratio of the total number of emails processed through the service to the number of emails in the particular category. The “Unknown” status means that the email address cannot be verified at the moment. Retrying later may succeed.
- Undeliverable: The number of emails in the “Undeliverable” category along with the percentage ratio of the total number of emails processed through the service to the number of emails in the particular category. The “Undeliverable” status means that the email address does not exist, is invalid, suspended, over quota, or disabled.
- Malformed: The number of emails in the “Malformed” category along with the percentage ratio of the total number of emails processed through the service to the number of emails in the particular category. The “Malformed” status means that the email address does not conform to a valid email format.
- SpamTrap: The number of emails in the “SpamTrap” category along with the percentage ratio of the total number of emails processed through the service to the number of emails in the particular category. The “SpamTrap” status means that an email address is not actively used by a real person but is set up or repurposed by email service providers, anti-spam organizations, or internet service providers to identify and catch spammers. You need to avoid SpamTrap emails at all costs. Those accounts are kept alive to damage the sender's reputation.
- Complainer: The number of emails in the “Complainer” category along with the percentage ratio of the total number of emails processed through the service to the number of emails in the particular category. Complainers commonly are users who like to complain after receiving an email. Complaints can vary from ISP notification to cease and desist letters. In some rare cases, they can also pursue litigation. These are valid addresses but we do not recommend sending mail.
- Bot: The number of emails in the “Bot” category along with the percentage ratio of the total number of emails processed through the service to the number of emails in the particular category. Bots are email accounts that are maintained by bot servers for sending spam, clicking every link, and other harmful or harmless activities.
- Seed Account: The number of emails in the “Seed Account” category along with the percentage ratio of the total number of emails processed through the service to the number of emails in the particular category. Seed accounts are known email addresses that are maintained in masses for various reasons. Most commonly they are used for compliance tracking.
- Disposable Email: The number of emails in the “Disposable Email” category along with the percentage ratio of the total number of emails processed through the service to the number of emails in the particular category. The “Disposable Email” status means that this is a temporary email account that is designed to only be used a few times before expiring.
- Suppressed: The number of emails in the “Suppressed” category along with the percentage ratio of the total number of emails processed through the service to the number of emails in the particular category. The “Suppressed” status means the email is in the known suppression list.
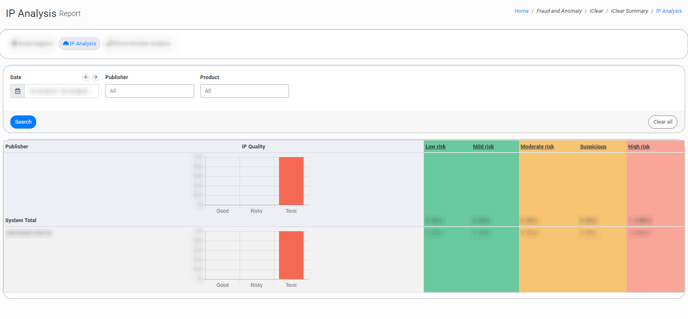
The “IP Analysis” tab
The “IP Analysis” tab allows you to view summary details about the “IP Analysis” third-party service results. The third-party service calculates a corresponding risk rate for each IP address that is processed.
Read more about the “IP Analysis” service in this Knowledge Base article.
You can narrow down the search results by using the following filters:
- Date: Select the date range of the report.
- Publisher: Select the Publisher.
- Product: Select the Product.
The report contains the following information. Please note that the first row of the report contains summary details across the system.
- Publisher: The name of the Publisher.
- IP Quality: The field contains the graph summarizing the results of service processing. The numbers are split by the general categories (Good, Risky, Toxic), and the total number of IP addresses processed through the system is a sum of the values in the Good, Risky, and Toxic columns. The detailed summary by metrics is displayed in the columns of the report.
- Low risk: The number of IP addresses in the “Low Risk” category along with the percentage ratio of the total number of IP addresses processed through the service to the number of IP addresses in the particular category. The “Low Risk” category is considered for the value range from 0 to 20. Users within this range pose a minimal threat and are generally considered safe. There's little to no evidence of suspicious or malicious behavior linked to their IP address.
- Mild risk: The number of IP addresses in the “Mid Risk” category along with the percentage ratio of the total number of IP addresses processed through the service to the number of IP addresses in the particular category. The “Mid Risk” category is considered for the value range from 21 to 50. Users within this range have shown some potential signs of risk, but not enough to categorize them as threatening. They may occasionally show evidence of unusual patterns, but not necessarily harmful activities, linked to their IP address. It's recommended to monitor activities, but not restrict access.
- Moderate risk: The number of IP addresses in the “Moderate Risk” category along with the percentage ratio of the total number of IP addresses processed through the service to the number of IP addresses in the particular category. The “Moderate Risk” category is considered for the value range from 51 to 74. Users within this range show a heightened level of risk. While they might not be directly involved in any malicious activities, there's a notable frequency of unusual behavior or patterns linked to IP addresses. It's advisable to pay close attention to their activities and verify their legitimacy.
- Suspicious: The number of IP addresses in the “Suspicious” category along with the percentage ratio of the total number of IP addresses processed through the service to the number of IP addresses in the particular category. The “Suspicious” category is considered for the value range from 75 to 87. Users within this range exhibit significant signs of risk or suspicious activities linked to their IP address. They are likely using a proxy, VPN, or TOR connection; while not all are malicious, there is an increased probability of being engaged in fraudulent activities.
- High risk: The number of IP addresses in the “High Risk” category along with the percentage ratio of the total number of IP addresses processed through the service to the number of IP addresses in the particular category. The “High Risk” category is considered for the value range from 88 to 100. Users within this range are considered very high risk. Their IP address has been associated with suspicious behavior signals, frequent abusive behavior, or engaged in recent or excessive malicious activities. They fit the profile of a typical risky user and require immediate attention or action.
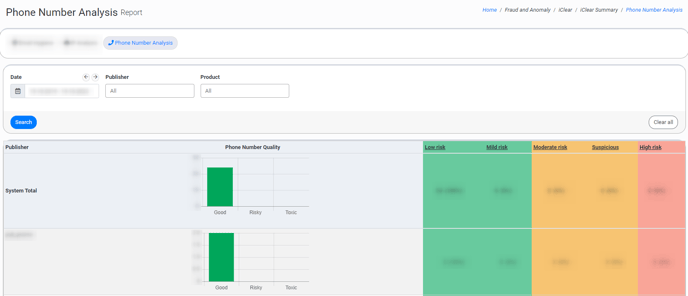
The “Phone Number Analysis” tab
The “Phone Number Analysis” tab allows you to view summary details about the “Phone Number Analysis” third-party service results. The third-party service calculates a corresponding risk rate for each phone number that is processed.
Read more about the “Phone Number Analysis” service in this Knowledge Base article.
You can narrow down the search results by using the following filters:
- Date: Select the date range of the report.
- Publisher: Select the Publisher.
- Product: Select the Product.
The report contains the following information. Please note that the first row of the report contains summary details across the system.
- Publisher: The name of the Publisher.
- Phone Number Quality: The field contains the graph summarizing the results of service processing. The numbers are split by the general categories (Good, Risky, Toxic), and the total number of phone numbers processed through the system is a sum of the values in the Good, Risky, and Toxic columns. The detailed summary by metrics is displayed in the columns of the report.
- Low risk: The number of phone numbers in the “Low Risk” category along with the percentage ratio of the total number of phone numbers processed through the service to the number of phone numbers in the particular category. The “Low Risk” category is considered for the value range from 0 to 20. Users within this range pose a minimal threat and are generally considered safe. There's little to no evidence of suspicious or malicious behavior linked to their phone number.
- Mild risk: The number of phone numbers in the “Mid Risk” category along with the percentage ratio of the total number of phone numbers processed through the service to the number of phone numbers in the particular category. The “Mid Risk” category is considered for the value range from 21 to 50. Users within this range have shown some potential signs of risk, but not enough to categorize them as threatening. They may occasionally show evidence of unusual patterns, but not necessarily harmful activities, linked to their phone number.
- Moderate risk: The number of phone numbers in the “Moderate Risk” category along with the percentage ratio of the total number of phone numbers processed through the service to the number of phone numbers in the particular category. The “Moderate Risk” category is considered for the value range from 51 to 74. Users within this range show a heightened level of risk. While they might not be directly involved in any malicious activities, there's a notable frequency of unusual behavior or patterns linked to their phone number.
- Suspicious: The number of phone numbers in the “Suspicious” category along with the percentage ratio of the total number of phone numbers processed through the service to the number of phone numbers in the particular category. The “Suspicious” category is considered for the value range from 75 to 87. Users within this range exhibit significant signs of risk or suspicious activities linked to their phone numbers. This may be related to previous reputational issues with the phone number, with evidence of potentially dangerous activities, but not necessarily fraudulent ones.
- High risk: The number of phone numbers in the “High Risk” category along with the percentage ratio of the total number of phone numbers processed through the service to the number of phone numbers in the particular category. The “High Risk” category is considered for the value range from 88 to 100. Users within this range are considered very high risk. Their phone numbers have been associated with suspicious behavior signals, frequent abusive behavior, or engagement in recent or excessive malicious activities. They fit the profile of a typical risky user and require immediate attention or action.
The “Companies House” tab
The Companies House Report provides a summary of the retrieved status of companies and their officers using the Companies House API. It indicates whether company information submitted via lead generation forms was found in the official Companies House register.
Note: This report is available only in UK instances where the Companies House API third-party service (available only for the UK region) is enabled. It allows you to retrieve and prefill the searched company and its officers' details on your form. Read more about the Form Builder Third Party / Validation Settings in the Knowledge Base article.
To view the Companies House report, go to the Fraud and Anomaly > iClear Summary section, and click the “Companies House” tab.
The “Companies House” report contains the following information:
- Publisher: The name of the Publisher.
- Total Companies: The total number of searched companies on the forms.
- Found Companies: The number of companies that appeared in the search results using the Companies House Public Data API.
- Not Found Companies: The number of search results that did not find any company on the forms using the Companies House Public Data API.
- Total Officers: The total number of searched officers on the forms.
- Found Officers: The number of officers that appeared in the search results using the Companies House Public Data API.
- Not Found Officers: The number of search results that did not find any officer on the forms using the Companies House Public Data API.
The “Totals” row at the bottom of the table shows the summary number for each column.
You can narrow down the search results using the following filters:
- Date: Select the date range of the report.
- Publisher Agent: Select the Publisher Agent.
- Publisher: Select the Publisher.
- Product: Select the Product.
-1.png?width=688&height=308&name=unnamed%20(30)-1.png)